 Cryptography is the process of communicating securely in an insecure environment – i.e. where other people can listen in and control the communication channel.
Cryptography is the process of communicating securely in an insecure environment – i.e. where other people can listen in and control the communication channel.
The message you wish to send is converted to a cipher text that appears to be gibberish unless you know the secret to unlocking it.
There are two main types of cryptography – symmetric and asymmetric.
Symmetric is the oldest form but not the most secure as it implies both the sender and the receiver are in control of the cipher – or the coding and decoding key. One of the most common & simplest forms of Cipher – similar to the one that Caesar used to communicate with his generals – is just shifting the message to be sent by a number of letters in the alphabet.
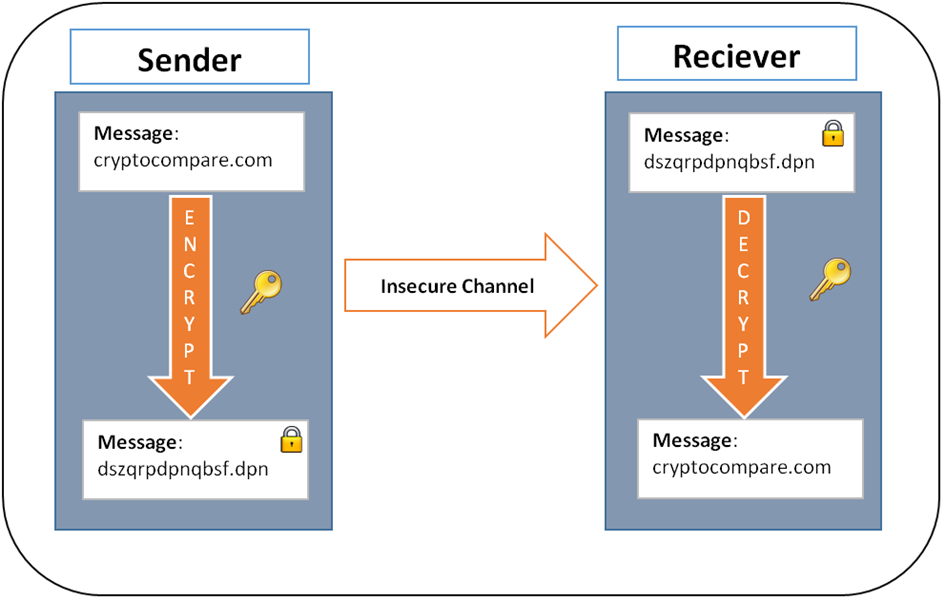
In the picture above the message, cryptocompare.com, is shifted by one letter in the alphabet – then sent across the insecure channel to the receiver who decrypts it using the same key – i.e. moving the letters one space to the start of the alphabet to decipher the text and reveal cryptocompare.com. These can be relatively easy to decode.
Symmetric cryptography has a problem - How to tell the other person what the code is? This has been dealt with somewhat by public key cryptography or essentially where the receiver generates a key pair and then sends the public key to the message sender. The sender then encrypts the message using the receivers public key and sends the encrypted message to the receiver. The receiver then takes the encrypted message and his private key and decrypts the message. This is asymmetric cryptography.
This method though can still be subject to the man in the middle attack unless there is some form of centralising authority who preside over keys and owners though certification – the most common uses of this are in SSL and TSL – Secure Socket Layer & Transport Security Layer.
Bitcoin and other crypto currencies use a form of digital signatures to take the process further by proving that the sender sent the message – i.e. non-repudiation – where the sender can’t deny that it was them who sent the message. The process is as shown here.
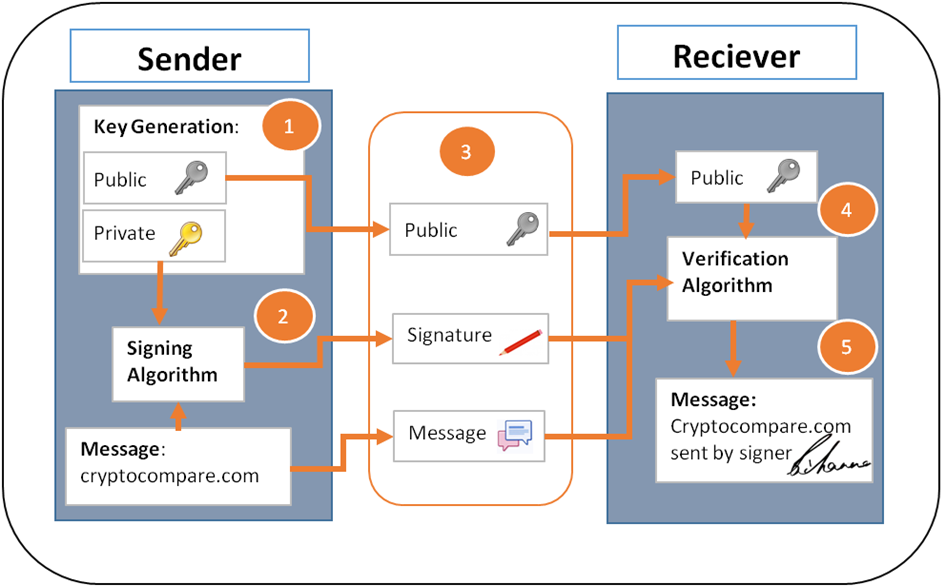
You may be asking how does the verification and signing algorithm work. Well this all has to do with elliptic curves and their properties and a mathematical trick– which basically means the Bitcoin Network can verify that a transaction was sent by the person who holds the private key without them revealing it!
Important information
This website is only provided for your general information and is not intended to be relied upon by you in making any investment decisions. You should always combine multiple sources of information and analysis before making an investment and seek independent expert financial advice.
Where we list or describe different products and services, we try to give you the information you need to help you compare them and choose the right product or service for you. We may also have tips and more information to help you compare providers.
Some providers pay us for advertisements or promotions on our website or in emails we may send you. Any commercial agreement we have in place with a provider does not affect how we describe them or their products and services. Sponsored companies are clearly labelled.













 Opera
Opera
 Safari
Safari