
As its name implies, a blockchain is a type of data structure that consists of a chain of blocks which contain information. This method of grouping data was originally conceived and described in 1991 by researchers who had initially planned to use a blockchain to timestamp digital documents.
The research team had used a blockchain to timestamp “digital documents so that it [was] not possible to backdate them or tamper with them.” This document management process is somewhat similar to how notarization of important files is performed.
Although the blockchain data structure was invented in the early 1990s by Dr. Stuart Haber and his colleagues, it wasn’t until 2008 that Satoshi Nakamoto, the pseudonymous inventor of Bitcoin (BTC), referenced blockchain in the Bitcoin whitepaper. This seminal whitepaper specified how blockchain, an immutable and distributed public ledger, would be used to implement the Bitcoin protocol, the world’s first peer-to-peer (P2P) “electronic cash system.”
Blockchain Data Is Immutable
One of the main properties of a blockchain allows data to be recorded, or registered, in a way that makes it very difficult to modify. Each block in a blockchain consists of a data set, the hash of that particular block, and the hash value of the previous block. The type of data stored in each block depends on the kind of blockchain network that has been implemented.
For example, the Bitcoin blockchain stores details about transactions (TX) which are broadcasted over the cryptocurrency’s network. These TX details include important information such as the amount of coins to be transferred and the addresses of the recipient and the sender. Additionally, the date and time when the TX was finalized is recorded with other information associated with each BTC payment.
Blocks Are Associated With Provably Unique Hash Values
Each block on a distributed ledger technology (DLT)-based network also contains a unique hash value which is comparable to a person’s fingerprint. That’s because all hashes associated with blocks uniquely identify a particular block and its contents. After a block has been generated on a DLT-based network, the platform’s algorithm invokes a hash function in order to compute the new block’s unique hash value.
Should the data inside a block be altered or replaced, then its associated hash value will also change automatically, or algorithmically. This feature makes hashes quite useful when trying to determine if a block’s contents have been modified. If the hash value associated with a block changes, then it can no longer be considered (by the system) to be the same block.
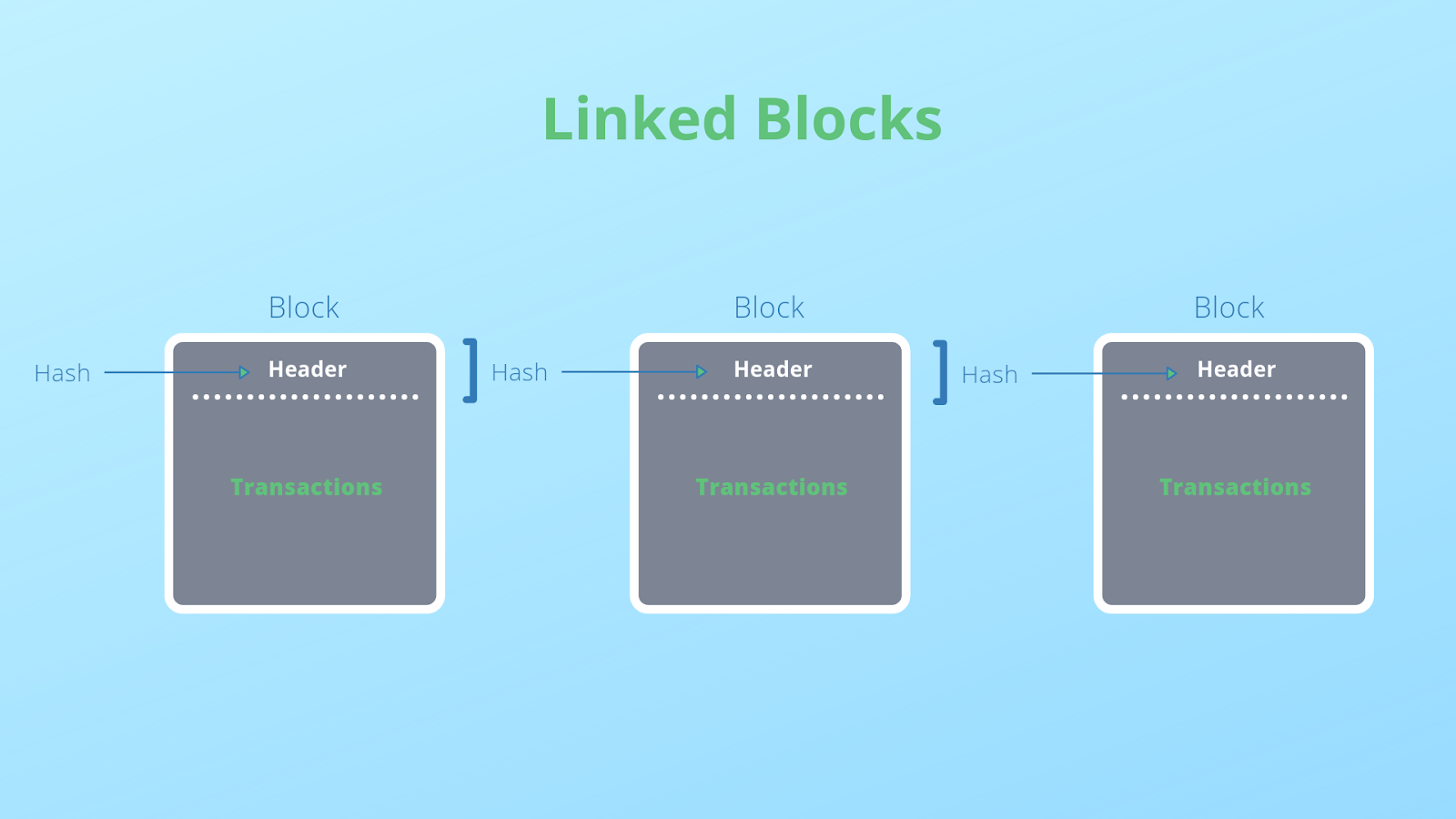
A block on a DLT network also contains the hash value of the previous block, and this creates a link or chain of blocks. It’s this particular data organization and management technique which helps in maintaining the integrity and security of data on a blockchain network.
What Is A Genesis Block?
All blocks that form a blockchain point to the previous block, however the genesis block does not point to a previous block because it’s the very first that is produced on a blockchain.
In the event that a user changes the contents of a block, the hash of that block will also change - in order to notify other users that the data in that particular block has been changed. Because all blocks are linked to each other on a DLT-based network, the data in all other blocks that come after the corrupted block will also be considered invalid.
Blocks become invalid because they no longer contain a valid hash value after previous block(s) on a DLT-enabled platform have been corrupted. However, strictly using cryptographic hashes to protect the integrity of data is no longer sufficient due to advances in modern computing algorithms. For instance, a malicious entity could potentially tamper with a block by recomputing all hash values on a DLT-powered network. This would effectively allow a bad actor to make all blocks on a blockchain appear valid again.
Proof Of Work Algorithms Further Secure Blockchains
In order to prevent malicious users from exploiting a DLT-based platform in this manner, blockchain networks use proof-of-work (PoW) algorithms. These act as mechanisms which help in slowing down the process, or rate at which new blocks are generated on a DLT-enabled network, as well as making it hard for bad actors to take control of a blockchain network.
For instance, it takes an average of 10 minutes on the Bitcoin network to perform the required “proof of work” for appending a new block to the cryptocurrency’s chain. Assuming that a blockchain platform is able to maintain adequate hashing power, it becomes practically difficult to tamper with blocks on its network. That’s because if a user attempts to alter the contents of one block on a chain, then they’ll have to recompute the “proof of work” for all subsequent blocks.
Therefore, it can be argued that the security of a blockchain is maintained by its hashing algorithm and its PoW protocol. Additionally, blockchains are further secured due to their distributed nature, or implementation. Instead of relying on a central management system, a blockchain is based on a peer-to-peer (P2P) technology network which is accessible (public) to everyone.
Those who participate on a public blockchain platform can access the full transaction history of that particular network. The nodes, or network participants, on a DLT-powered platform can use the transaction logs to verify the integrity of a blockchain’s data.
What Happens When A New Block Is Created?
When a new block is produced on a blockchain platform, that particular block is sent or broadcast to all network participants. Each user on the DLT network can independently verify whether the information contained in that block is accurate and whether it has been corrupted. If a block contains valid transaction data, then each participant on a blockchain appends that new block to the blockchain of that particular network.
When all nodes on a blockchain come to an agreement, commonly referred to as consensus, regarding which block(s) are valid and eligible for processing, then those blocks are validated by full-node operators or miners. Corrupt blocks are rejected by honest network participants and it’s also very difficult to tamper with blockchain data. That’s because a user would have to tamper with all blocks on a DLT network by recomputing the proof of work for every block on the chain.
Moreover, a user would have to take control of over 50% of a blockchain network’s hashing power - before they can permanently modify data on the distributed platform. When a malicious user is effectively able to launch what are referred to as 51% attacks, then that’s when their tampered blocks can be appended to the affected blockchain’s transaction log.
Additional Functionality Constantly Being Added To Blockchains
Because it’s practically unfeasible in most cases to launch such attacks on blockchains which have a strong network effect such as Bitcoin (BTC) and Ethereum (ETH), there’s almost no chance that users’ data and other digital assets might be stolen or compromised.
The blockchain industry is one of the world’s fastest growing industries and new security protocols are constantly being developed. Software architects throughout the world continue to work on implementing additional functionality on blockchains including implementing smart contracts. These are automated business logic programs that make decisions on behalf of users or their owner(s) based on a specific set of conditions.
Important information
This website is only provided for your general information and is not intended to be relied upon by you in making any investment decisions. You should always combine multiple sources of information and analysis before making an investment and seek independent expert financial advice.
Where we list or describe different products and services, we try to give you the information you need to help you compare them and choose the right product or service for you. We may also have tips and more information to help you compare providers.
Some providers pay us for advertisements or promotions on our website or in emails we may send you. Any commercial agreement we have in place with a provider does not affect how we describe them or their products and services. Sponsored companies are clearly labelled.













 Opera
Opera
 Safari
Safari